
Hardware Trojan Detection and Mitigation
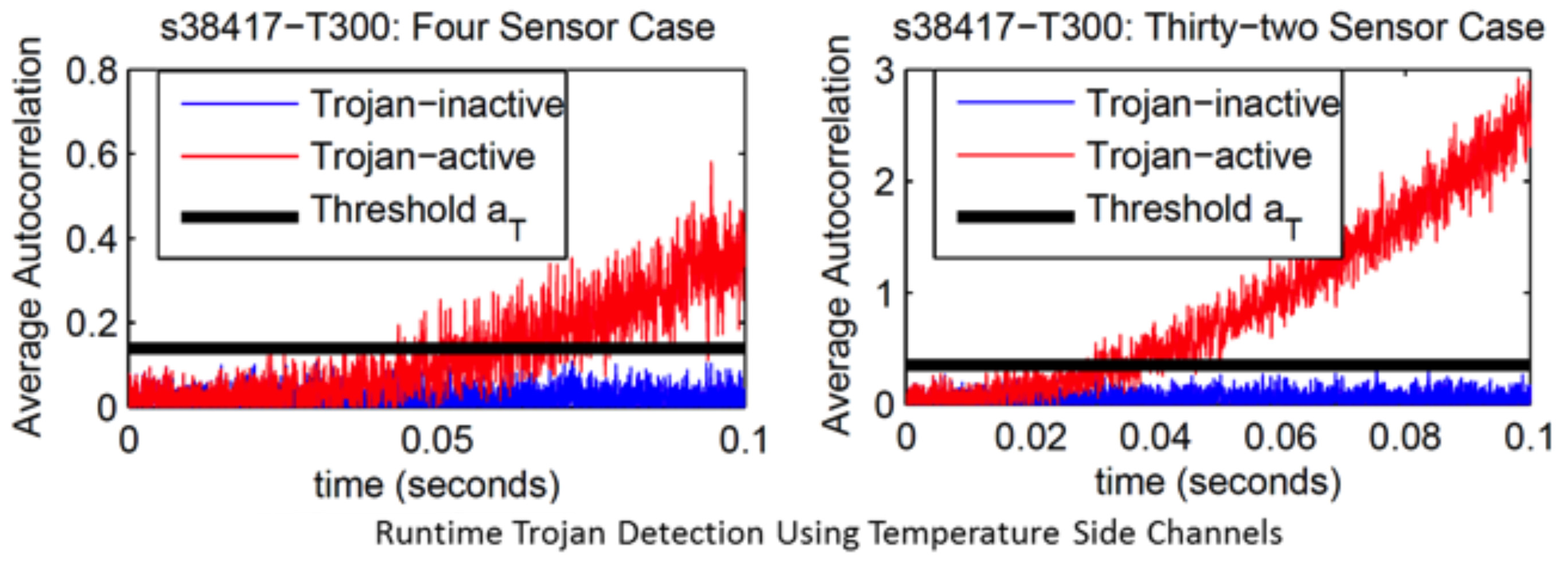
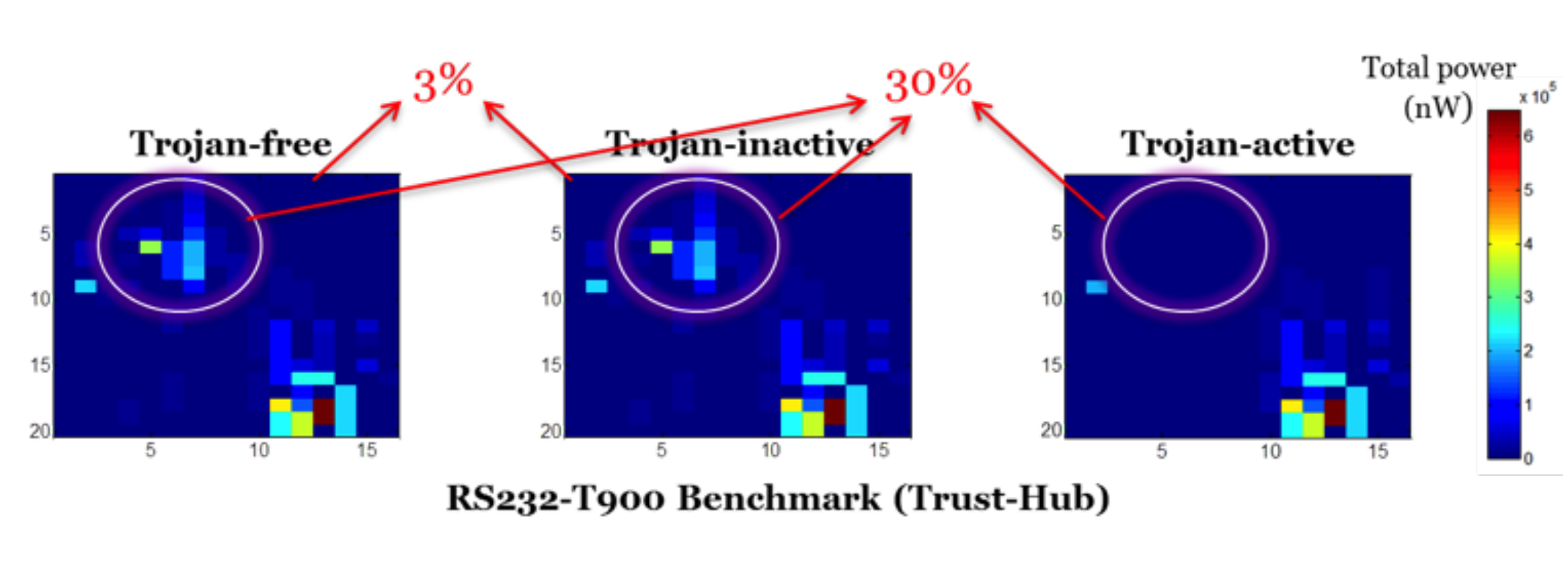
Hardware Trojans represent malicious circuitry incorporated within modern ICs which can potentially steal sensitive information and/or render the chip useless. We have developed a host of techniques for detection and mitigation of hardware Trojans. Some of these techniques rely on post silicon reverse engineering based approaches. Others use runtime measurements of signals such as temperature to detect anomalies stemming from Trojan activity.
-
Domenic Forte, Chongxi Bao, Ankur Srivastava: Temperature Tracking. “An Innovative Run-time Approach for Hardware Trojan Detection”. Proceedings of the International Conference on Computer-Aided Design (ICCAD), November 2013.
-
Chongxi Bao, Domenic Forte, Ankur Srivastava. “On Application of One-class SVM to Reverse Engineering-Based Hardware Trojan Detection”. Proceedings of the International Symposium on Quality Electronic Design (ISQED), March 2014.
-
Chongxi Bao, Yang Xie, Ankur Srivastava. “A Security-aware Design Scheme for Better Hardware Trojan Detection Sensitivity”. Hardware-Oriented Security and Trust (HOST), IEEE International Symposium on, May 2015.
-
Chongxi Bao, Domenic Forte, Ankur Srivastava: Temperature Tracking. “Towards Robust Run-time Detection of Hardware Trojans”. Computer-Aided Design of Integrated Circuits and Systems (TCAD), IEEE Transactions on 34.10 (2015): 1577-1585.
-
Chongxi Bao, Domenic Forte, Ankur Srivastava. “On Reverse Engineering-Based Hardware Trojan Detection”. Computer-Aided Design of Integrated Circuits and Systems (TCAD), IEEE Transactions on, 35.01 (2016): 49-57.




